How to Root Asus Memo Pad ME172V
Announced back in 2013, Asus Memo Pad ME172V is well-suited for a rooting. How can you do that? Find the answer below.
Your Asus Memo Pad ME172V has an Android 4.1 OS and a 1 GHz VIA WM8950 processor among many other specifications. SRSRoot is the method which is the best one to use with any device. This tool works with whatever Android your gadget’s using; so you won’t lose the 4.0.3 version your tablet’s currently running after its rooting is over.
The following Build ID is the one we’ve used for the procedure: asus-ME172V-WW_user_4.5.4.31116393_20130910. If you want to try out other Build IDs, you can. That’s one of the beauties of using the SRSRoot tool. The latter also wins points for being compatible with many other gadget brands.
The improvements
In case you don’t like how your device acts with root access on it, this application is a great way to unroot the tablet. To install the new tool on the latter, you don’t need money. The method used here offers admin and superuser level permission and it’s powered by SRS Server.
A rooted tablet has many advantages over a gadget that’s untouched. For one, your device will become easy to customize; the new tool has some great customization options you can use. Then there’s the fact that your gadget can familiarize itself with root-only apps and custom ROMs. Very soon you’ll also be able to get in touch with some brand new features. Use only the Asus Memo Pad ME172V for this procedure; otherwise you’ll have a bricked tablet to deal with. Thanks to root access, your tablet will last more, its CPU will be faster and the whole performance will be improved.
After your tablet’s rooted, you may think of getting the most recent Android version on it. If an update is on your mind, be sure to prepare for some damage. The first to be deleted are the root access and system partition. If you don’t decide for an update, the tablet’s warranty will be taken away from it. Everything else will be OK.
Prerequisites
Let’s have a quick look at these pre-requisites:
- the data your tablet is storing must be saved, which means you should create a backup;
- a full NANDroid backup is needed, to, so be sure to also generate one for the Asus ME172V;
- charge the tablet’s battery;
- the operating system used by your notebook must be Windows;
- go to this location and download USB drivers on your notebook;
- the security software on your tablet should be disabled;
- the notebook’s security software must be disabled, as well;
- be sure to enable USB Debugging on the tablet.
Step by step instructions
Time to get the rooting going. We have this first step for you to follow.
- Do this: download the SRSRoot software from a certain web page; don’t go somewhere else, this is the only place you’ll find the correct software for your tablet. When you’re on the page we recommended, tap a download button located there.
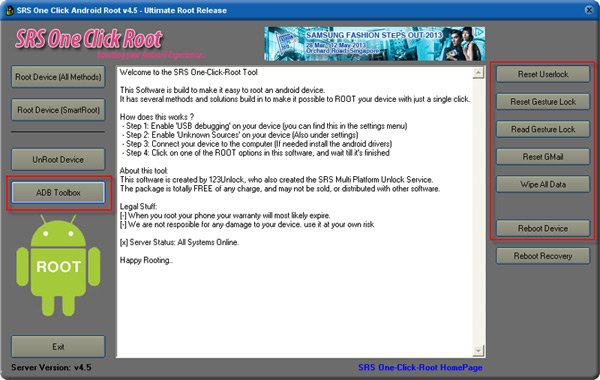
- The tool will then start its download phase on your notebook. After this is over, the application will get flashed on the notebook.
- You then have to open it there and move on. Which means you have to enable Unknown Sources on the tablet. Do that by taking this route: tap Menu, then tap Settings, look for the option in questions and click on it.
- When it’s turned on, enable USB Debugging if you haven’t done it for our previously mentioned requirements. Manage a connection between the Asus Memo Pad ME172V and your notebook.
- [sc name=”banner-jos”]To generate this, make use of your tablet’s personal USB cable and then have patience. A connection will then be established, so tap this option: Click on Root Device (All Methods).
- Your gadget will then enter the much-needed rooting phase. Give it a few minutes to finish.
After the process finally ends, you will have the chance to enjoy the rooting novelties you’ve heard so much about. But first, restart the tablet. If nothing happens, you should repeat the tutorial from step one all the way to the last step.
If you reach a point where you don’t understand our steps, you can ask us anything about them in the comment box below.





